HarmonyOS 鸿蒙Next:通用密钥库导入SM2密钥对是否参考ECC密钥对材料格式,Z坐标含义是什么?
HarmonyOS 鸿蒙Next:通用密钥库导入SM2密钥对是否参考ECC密钥对材料格式,Z坐标含义是什么? 已解决!
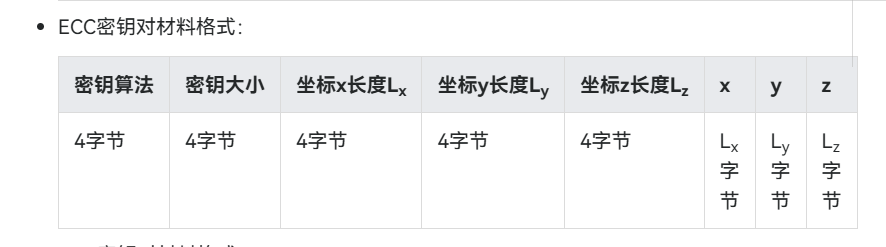
答案如下:
导入SM2密钥成功,z坐标就是d,能够正常加解密,以下是密钥材料格式,供大家参考
x=78529709012237989470648005562158956873367078096996658413595646418346794218200
y=44571171034297342044934241533793805592126578225310445969376746905136045509346
d=64701542618614937596731246738981859067984663244448522747546152468606387942849
0x96,0x00,0x00,0x00, // 密钥ID 150 小端序
0x00,0x01,0x00,0x00,// 密钥长度 256 小端序
0x20,0x00,0x00,0x00,// x长度 32 小端序
0x20,0x00,0x00,0x00,// y长度 32 小端序
0x20,0x00,0x00,0x00,// d长度 32 小端序
0xAD,0x9E,0x3D,0x7C,0xCC,0x82,0x77,0x9C,0x91,0x60,0xB9,0x50,0x7E,0x10,0x43,0xF6,
0xD4,0x6A,0xB2,0x5B,0xF0,0x11,0x8E,0xAA,0x4B,0x64,0xE8,0x68,0x82,0xF2,0xD8,//x 大端序
0x62,0x8A,0x63,0x89,0x70,0x04,0x6A,0x7B,0x64,0x62,0xA1,0x8F,0xE0,0x95,0xA5,0xC3,
0x43,0x8C,0x27,0x56,0xC4,0x77,0xCD,0x42,0x46,0x4F,0xB4,0x41,0x26,0x68,0x4A,0xE2,//y 大端序
0x8F,0x0B,0xC6,0x7E,0x66,0x39,0x15,0xCF,0x9F,0xB8,0x15,0xA7,0x73,0x69,0x8C,0xE0,
0x11,0x88,0x56,0xCE,0x41,0x6B,0x9D,0x6A,0x08,0xB7,0x6F,0x3A,0xAD,0x4E,0xF5,0xC1 //d 大端序
更多关于HarmonyOS 鸿蒙Next:通用密钥库导入SM2密钥对是否参考ECC密钥对材料格式,Z坐标含义是什么?的实战系列教程也可以访问 https://www.itying.com/category-93-b0.html
// x 109471080080593182227376980267518856903983425945963778445678662979399694245764 // y 16084280609150518971473135238929744201500993413878085560039228131709400021784 // d 99123125648259591304421671921836665866603574703236924699195108187636133599958
x y d 都是BigInteger ,组织成
let result=new Uint8Array([ 0x96,0x00,0x00,0x00,//SM2 算法ID 150 0x00,0x01,0x00,0x00,// 密钥长度 256 0x20,0x00,0x00,0x00, //x 长度 32 0x20,0x00,0x00,0x00, //y 长度 32 0x20,0x00,0x00,0x00, //d 长度32 0x84,0x5F,0x25,0xED,0x89,0xE5,0xBA,0x87,0x6C,0x5F,0xAF,0xA8,0x1F,0xC3,0x52,0x2C, 0x73,0xD8,0x10,0xE6,0x12,0x40,0xEB,0x5D,0xB3,0xC3,0xC4,0x92,0x83,0x6F,0x06,0xF2,
0x18,0x7B,0x06,0xA0,0x07,0x19,0x29,0xC5,0xDE,0x66,0xE1,0x60,0x88,0x21,0xB3,0x37, 0x14,0xE7,0xD0,0x34,0x29,0x2A,0x8F,0x98,0x0A,0xDB,0xFF,0xA5,0x55,0x61,0x8F,0x23,
0xD6,0x1A,0xE1,0x10,0x6D,0x66,0xD1,0xF5,0xA9,0x13,0x8C,0xB3,0xAD,0xAE,0x11,0x3B, 0x33,0x83,0xC6,0x08,0x5C,0xD3,0x70,0x5B,0x47,0x76,0x82,0x4C,0x71,0xB3,0x25,0xDB ]); 看看转换的对么?导入 报参数错误
更多关于HarmonyOS 鸿蒙Next:通用密钥库导入SM2密钥对是否参考ECC密钥对材料格式,Z坐标含义是什么?的实战系列教程也可以访问 https://www.itying.com/category-93-b0.html
试下这个,秘钥要转成16进制,可以用这个网站:https://the-x.cn/encodings/Hex.aspx:
let rsa2048PrivateKeyMaterial = new Uint8Array([ 0x96, 0x00, 0x00, 0x00, // 密钥算法:huks.HuksKeyAlg.HUKS_ALG_SM2 = 150 0x00, 0x01, 0x00, 0x00, // 密钥大小(比特):256 0x4e, 0x00, 0x00, 0x00, // 坐标x长度(字节):78 0x4d, 0x00, 0x00, 0x00, // 坐标y长度(字节):77 0x4d, 0x00, 0x00, 0x00, // 坐标z长度(字节):77 // x坐标 0x31,0x30,0x39,0x34,0x37,0x31,0x30,0x38,0x30,0x30,0x38,0x30,0x35,0x39,0x33,0x31, 0x38,0x32,0x32,0x32,0x37,0x33,0x37,0x36,0x39,0x38,0x30,0x32,0x36,0x37,0x35,0x31, 0x38,0x38,0x35,0x36,0x39,0x30,0x33,0x39,0x38,0x33,0x34,0x32,0x35,0x39,0x34,0x35, 0x39,0x36,0x33,0x37,0x37,0x38,0x34,0x34,0x35,0x36,0x37,0x38,0x36,0x36,0x32,0x39, 0x37,0x39,0x33,0x39,0x39,0x36,0x39,0x34,0x32,0x34,0x35,0x37,0x36,0x34, // y坐标 0x31,0x36,0x30,0x38,0x34,0x32,0x38,0x30,0x36,0x30,0x39,0x31,0x35,0x30,0x35,0x31, 0x38,0x39,0x37,0x31,0x34,0x37,0x33,0x31,0x33,0x35,0x32,0x33,0x38,0x39,0x32,0x39, 0x37,0x34,0x34,0x32,0x30,0x31,0x35,0x30,0x30,0x39,0x39,0x33,0x34,0x31,0x33,0x38, 0x37,0x38,0x30,0x38,0x35,0x35,0x36,0x30,0x30,0x33,0x39,0x32,0x32,0x38,0x31,0x33, 0x31,0x37,0x30,0x39,0x34,0x30,0x30,0x30,0x32,0x31,0x37,0x38,0x34, // z坐标 0x39,0x39,0x31,0x32,0x33,0x31,0x32,0x35,0x36,0x34,0x38,0x32,0x35,0x39,0x35,0x39, 0x31,0x33,0x30,0x34,0x34,0x32,0x31,0x36,0x37,0x31,0x39,0x32,0x31,0x38,0x33,0x36, 0x36,0x36,0x35,0x38,0x36,0x36,0x36,0x30,0x33,0x35,0x37,0x34,0x37,0x30,0x33,0x32, 0x33,0x36,0x39,0x32,0x34,0x36,0x39,0x39,0x31,0x39,0x35,0x31,0x30,0x38,0x31,0x38, 0x37,0x36,0x33,0x36,0x31,0x33,0x33,0x35,0x39,0x39,0x39,0x35,0x38 ]);
没有Z坐标吧,问下这个材料是哪里的呀,可以麻烦发个链接不
你好,刚问过了,文档里面:x和y是公钥,z是私钥,z就是d。
SM2 bouncycastle生成的密钥对,参数如下:
- x=4248557222935418650622612101700285796301711927203677438305599826097867298875
- y=2390954386912924777403380282000050837511844101361549311500826181827555517668
- d=82733833807054129376160599093790298164704455913124035841415941780386589676191
看示例密钥对的导入材料,应该是使用的小端序,能否使用我提供的这几个数,用arkts组织个密钥对材料,看能不能导入呢,能导入的话,麻烦贴个代码,看看怎么组织的?
在HarmonyOS鸿蒙Next系统中,通用密钥库导入SM2密钥对时,确实会参考ECC(椭圆曲线密码学)密钥对的材料格式。这是因为SM2算法本身也是一种基于椭圆曲线的公钥密码算法,因此其密钥对的存储和导入格式与ECC密钥对有相似之处。
关于Z坐标的含义,在椭圆曲线密码学中,一个点的坐标通常由(X, Y)表示,但在某些情况下,如扩展坐标表示或特定的算法实现中,可能会引入额外的Z坐标。在SM2算法中,虽然通常使用(X, Y)坐标来表示椭圆曲线上的点,但Z坐标在某些运算或表示中也可能出现,主要用于实现投影坐标下的椭圆曲线运算,以提高运算效率。
然而,在通用密钥库导入SM2密钥对的上下文中,Z坐标通常不是直接关注的重点。导入过程主要关注的是密钥对的正确性、完整性和与系统的兼容性。因此,在导入SM2密钥对时,应确保密钥对符合系统要求的格式,并正确解析X和Y坐标。
如果问题依旧没法解决请联系官网客服,官网地址是:https://www.itying.com/category-93-b0.html








